January 3rd, 2026
Excalibur v1.2.0
The day threat models stopped being documents
Until now, threat modeling tools have had a quiet flaw.
They look structured.
But underneath, they behave like folders of text.
Threats over here.
Controls over there.
Attack scenarios copied into documents, frozen in time.
Useful but disconnected.
Excalibur v1.2.0 is where that ends.
Act I — When We Realised the Model Was Lying
We kept running into the same problem.
Threat data lived in two worlds:
Structured tables with no understanding of relationships
Graphs rich in relationships but missing context and metadata
Depending on where we pulled from, something was always missing.
So the threat model wasn’t wrong.
It was incomplete.
That’s when we stopped treating threat models as documents.
And started treating them as systems.
Act II — Everything Becomes a Node
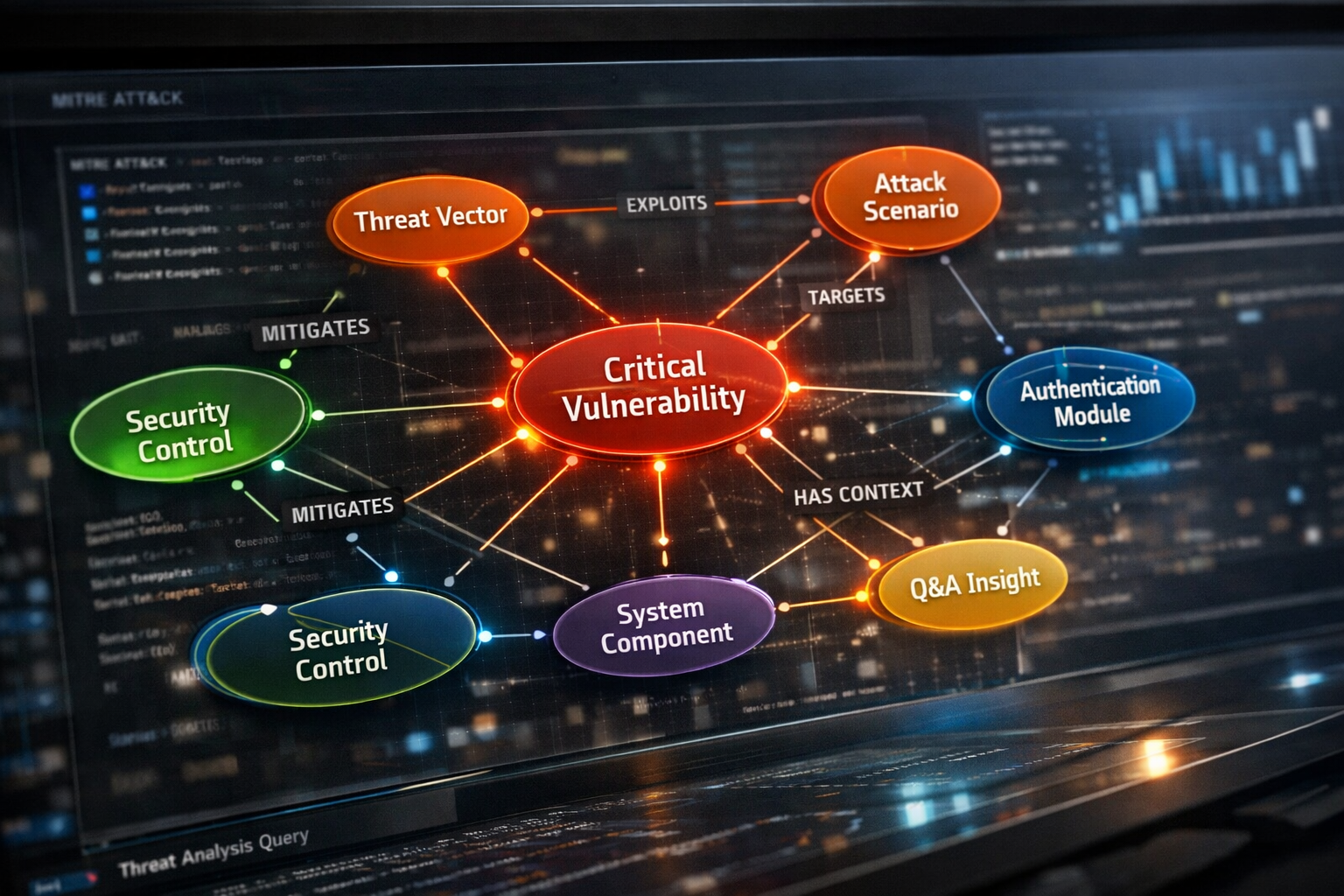
In v1.2.0, Excalibur’s threat modeling engine becomes a living knowledge graph.
Every meaningful thing now exists as a first-class citizen:
Threats
Attack scenarios
Components
Security controls
Context
Q&A
They aren’t blobs of JSON anymore.
They’re nodes, connected by intent.
An attack doesn’t just exist.
It targets a component.
It exploits a threat vector.
It’s mitigated by controls.
For the first time, you can ask questions like:
“What attacks touch authentication?”
“Which threats connect these two attack paths?”
“What controls actually mitigate high-likelihood vectors?”
And get real answers.
Not text search. Not filters. Just Relationships.
Act III — One Brain, Not Two Half-Brains
Behind the scenes, something subtle but important changed.
Excalibur used to think in two places:
Structured data from Supabase
Relationship data from Neo4j
They didn’t disagree.
They just didn’t talk.
v1.2.0 introduces a unified retrieval layer that pulls from both, in parallel, then intelligently merges the results.
Duplicates are removed.
Context is scored.
Signals are ranked.
The system finally sees the whole picture at once.
This is what “unified security intelligence” actually means.
Act IV — Attacks Learn to Remember Each Other
Attack scenarios are no longer isolated exercises.
Every attack now lives in the graph.
Which means:
Attacks can reference shared threat vectors
Chains emerge naturally
Patterns surface over time
Two attacks exploiting the same weakness now know they’re related.
The system can reason about escalation paths without being explicitly told.
This is where the model starts to feel less like a tool and more like an analyst who remembers past work.
Act V — Intelligence That Knows When to Think Hard
As the graph grew smarter, the intelligence layer had to mature too.
v1.2.0 adds capability-based LLM routing.
Excalibur no longer asks:
“Which model should we use?”
It asks:
“What kind of thinking is required?”
Reasoning tasks go to reasoning models.
Fast generation goes where speed matters.
Local models stay local when privacy demands it.
And when multiple sources disagree, a Judge Agent steps in — comparing results for completeness, accuracy, and actionability.
Not all answers are equal anymore.
The system knows that too.
Act VI — Seeing the Graph Clearly
A living graph is only useful if you can read it.
So we rebuilt the visualization layer:
Cleaner nodes where content matters
Rich panels that show full context in markdown
Darker edges so relationships are visible at a glance
A larger canvas with deeper zoom
A clearer legend that separates threats, attacks, and controls
The graph stopped feeling crowded.
And started feeling navigable.
Act VII — The Boring Work That Makes Everything Trustworthy
Some of the most important changes aren’t visible.
v1.2.0 quietly:
Normalises threat terminology so the database stays consistent
Resolves missing foreign keys automatically
Removes hundreds of lines of dead code
Makes the system easier to reason about and harder to break
Nothing flashy.
Everything necessary.
What v1.2.0 Really Is
This release isn’t about more features.
It’s about a shift in how security knowledge exists inside Excalibur.
Threat models are no longer files you generate and forget.
They’re living systems that evolve, connect, and compound over time.
From fragmented data
to unified intelligence.
From documents to understanding.
Welcome to Excalibur v1.2.0.