January 19th, 2026
New
Improved
Fixed

Intelligence Infrastructure & Platform Maturity
TL;DR
We’re not adding more security noise to an already crowded industry. We’re stripping cybersecurity back to first principles and rebuilding it as an intelligence system that actually understands what it’s protecting.
Instead of fragmented tools, static reports, and guesswork, Excalibur connects architecture, threats, attacks and controls into one living system. Faster insight, clearer decisions, and security work that finally scales without losing human judgement.
This isn’t a quick win or a feature race.
We’re doing the hard, unglamorous work to change how cybersecurity is built and we’re not stopping.
If this industry is going to be transformed, it won’t be by shortcuts.
It’ll be by systems that think clearly and teams that refuse to quit.,
Excalibur just moved from generating security artifacts to operating as an intelligence platform. Which is one more step towards Cyber Artificial General Intelligence.
v1.3.0 focuses on four pillars:
Neural network reasoning (The central brain which learns more and more about your product and company all privately!)
Flexible, customer-owned AI infrastructure
Human-guided offensive workflows (Yes we are diving into offensive more in the coming updates)
Platform reliability at production scale
🧠 Neural Network-Native Gap Analysis
18× faster, zero guesswork
What changed
Gap Analysis(previously clarifying questions) is now executed directly against the Knowledge base
No slow LLM loops
No generic “clarifying questions”
What it detects (automatically)
External attack paths without authentication
Threats with no mitigations
Components missing security controls
Data flows without sensitivity labels
Orphaned components and empty trust boundaries
Areas with no Q&A coverage
Incomplete or undocumented nodes
Why it matters
Response time dropped from ~18 seconds to ~1 second
Findings are precise, contextual, and architecture-aware
Questions now reflect what’s missing, not what’s easy to ask
🔄 LLM Provider Flexibility
You own the intelligence layer
What changed
Full migration to OpenRouter from Runpod
Unified access to 500+ LLM providers
Bring-Your-Own-AI via Settings UI
Enterprise Azure Ai and AWS Bedrock support incoming
Improvements
Higher token limits for reasoning-heavy tasks
Better reliability under load
Cleaner support for structured outputs
Important note
Users must configure AI providers via Settings → AI Providers before proceeding
🤖 Pentesting Agent (Human-in-the-Loop)
Automation without autonomy
New capability
AI-assisted pentesting agent with explicit approval gates
Workflow
Scoped targets
Human-approved interpretation
Structured attack planning
Step-by-step execution with approvals
Automatic results compilation
Why this matters
No black-box agents,
No uncontrolled execution
Clear intent, traceability, and human ownership at every step
🏗️ Architecture & Context Intelligence
Deeper extraction, cleaner signal
Architecture ingestion
Multi-phase extraction pipeline for higher fidelity
Better component discovery
More accurate connection mapping
Validation and retry logic built-in
Context ingestion
Documents now understand architecture
Context links to specific components
Coverage and completeness become measurable
New capabilities
Component-aware chunking
Graph-linked documentation
Validation endpoints for ingestion quality
🔐 HackerOne Integration
Bug bounty visibility, inside the platform
New dashboard
Live HackerOne integration
Severity breakdowns
Report detail views
Safe fallback when credentials aren’t present
Why this matters
External findings now sit alongside internal threat models
Less tab-hopping
Better prioritisation
🐛 Stability & Reliability Fixes
Production-grade by default
Fixed JSON extraction issues for reasoning models
Stabilised Neo4j connection pooling in long-running deployments
Resolved rate-limiter crashes on newer FastAPI versions
Fixed canvas graph persistence edge cases
Corrected observability and tracing initialisation
Repaired state mismatches in Gap Analysis answers
🧪 Testing & Delivery Infrastructure
End-to-end tests for core workflows
Automated CI/CD validation
Deployment status notifications
Safer, more predictable releases
📊 Release Metrics in past 2 weeks
60+ commits
7 major features
15+ fixes
100+ files changed
18× performance improvement in Gap Analysis
What v1.3.0 really represents
This release isn’t about more automation.
It’s about better intelligence, faster feedback, and tighter control.
Less guessing.
More grounding.
More trust in the system.
Excalibur is growing up and we wont stop until we reached artificial general intelligence in cybersecurity.
January 3rd, 2026
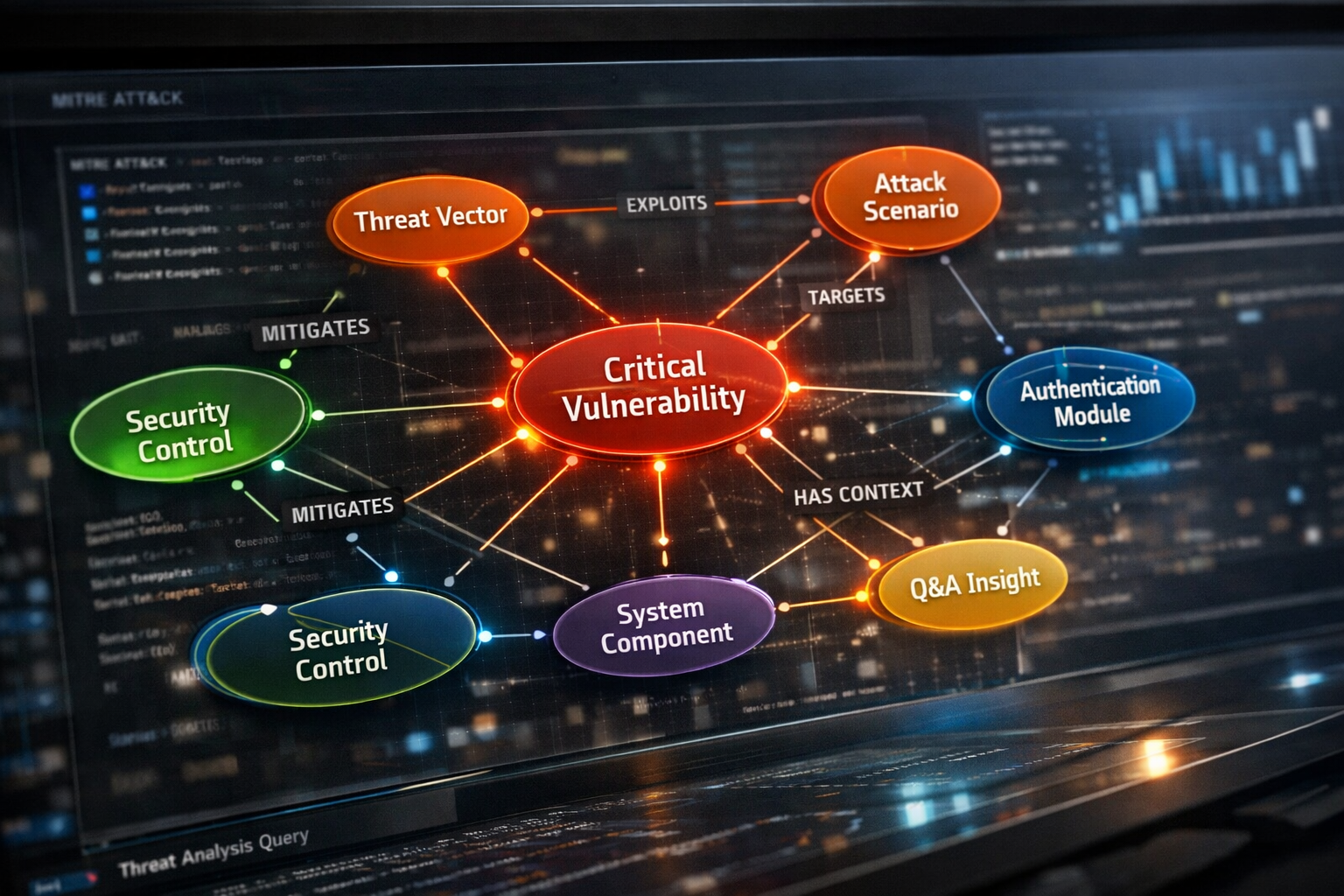
The day threat models stopped being documents
Until now, threat modeling tools have had a quiet flaw.
They look structured.
But underneath, they behave like folders of text.
Threats over here.
Controls over there.
Attack scenarios copied into documents, frozen in time.
Useful but disconnected.
Excalibur v1.2.0 is where that ends.
Act I — When We Realised the Model Was Lying
We kept running into the same problem.
Threat data lived in two worlds:
Structured tables with no understanding of relationships
Graphs rich in relationships but missing context and metadata
Depending on where we pulled from, something was always missing.
So the threat model wasn’t wrong.
It was incomplete.
That’s when we stopped treating threat models as documents.
And started treating them as systems.
Act II — Everything Becomes a Node
In v1.2.0, Excalibur’s threat modeling engine becomes a living knowledge graph.
Every meaningful thing now exists as a first-class citizen:
Threats
Attack scenarios
Components
Security controls
Context
Q&A
They aren’t blobs of JSON anymore.
They’re nodes, connected by intent.
An attack doesn’t just exist.
It targets a component.
It exploits a threat vector.
It’s mitigated by controls.
For the first time, you can ask questions like:
“What attacks touch authentication?”
“Which threats connect these two attack paths?”
“What controls actually mitigate high-likelihood vectors?”
And get real answers.
Not text search. Not filters. Just Relationships.
Act III — One Brain, Not Two Half-Brains
Behind the scenes, something subtle but important changed.
Excalibur used to think in two places:
Structured data from Supabase
Relationship data from Neo4j
They didn’t disagree.
They just didn’t talk.
v1.2.0 introduces a unified retrieval layer that pulls from both, in parallel, then intelligently merges the results.
Duplicates are removed.
Context is scored.
Signals are ranked.
The system finally sees the whole picture at once.
This is what “unified security intelligence” actually means.
Act IV — Attacks Learn to Remember Each Other
Attack scenarios are no longer isolated exercises.
Every attack now lives in the graph.
Which means:
Attacks can reference shared threat vectors
Chains emerge naturally
Patterns surface over time
Two attacks exploiting the same weakness now know they’re related.
The system can reason about escalation paths without being explicitly told.
This is where the model starts to feel less like a tool and more like an analyst who remembers past work.
Act V — Intelligence That Knows When to Think Hard
As the graph grew smarter, the intelligence layer had to mature too.
v1.2.0 adds capability-based LLM routing.
Excalibur no longer asks:
“Which model should we use?”
It asks:
“What kind of thinking is required?”
Reasoning tasks go to reasoning models.
Fast generation goes where speed matters.
Local models stay local when privacy demands it.
And when multiple sources disagree, a Judge Agent steps in — comparing results for completeness, accuracy, and actionability.
Not all answers are equal anymore.
The system knows that too.
Act VI — Seeing the Graph Clearly
A living graph is only useful if you can read it.
So we rebuilt the visualization layer:
Cleaner nodes where content matters
Rich panels that show full context in markdown
Darker edges so relationships are visible at a glance
A larger canvas with deeper zoom
A clearer legend that separates threats, attacks, and controls
The graph stopped feeling crowded.
And started feeling navigable.
Act VII — The Boring Work That Makes Everything Trustworthy
Some of the most important changes aren’t visible.
v1.2.0 quietly:
Normalises threat terminology so the database stays consistent
Resolves missing foreign keys automatically
Removes hundreds of lines of dead code
Makes the system easier to reason about and harder to break
Nothing flashy.
Everything necessary.
What v1.2.0 Really Is
This release isn’t about more features.
It’s about a shift in how security knowledge exists inside Excalibur.
Threat models are no longer files you generate and forget.
They’re living systems that evolve, connect, and compound over time.
From fragmented data
to unified intelligence.
From documents to understanding.
Welcome to Excalibur v1.2.0.
December 30th, 2025
New
Improved
Fixed

For People who like a story:
The platform learned how to choose. And how to protect itself.
V1 was about ground truth.
V1.1 is about control.
Control over where intelligence runs.
Control over who sees what.
Control over the small failure modes that quietly ruin trust.
This release isn’t flashy on the surface.
It’s decisive under the hood.
Act I: Excalibur Stops Betting on a Single Brain
In V1, Excalibur could think.
In V1.1, it can choose how to think.
We added true multi-provider LLM support.
You can now run Excalibur with:
NVIDIA DGX Cloud
RunPod serverless GPU inference
And more importantly, Excalibur doesn’t hardcode that decision.
LLM requests now route dynamically to the provider you configure.
Your infrastructure. Your cost model. Your risk tolerance.
No vendor lock-in disguised as “simplicity.”
And because visibility matters, the Settings UI now clearly shows which providers are wired in with proper branding, not guesswork.
Excalibur doesn’t assume where your intelligence should live anymore.
You decide.
Act II: Sharing Without Losing Ownership
Reports are meant to be read.
They’re also meant to be protected.
V1.1 deepens access control with RBAC Phase 2 and 3.
You can now:
Share reports with teammates through a dedicated access control interface
Give external viewers a guest, read-only experience
Manage share links without wondering who still has access
And we closed a dangerous edge case.
Owners can no longer accidentally downgrade themselves when sharing.
Because losing control of your own report should never be one click away.
Collaboration got easier.
Ownership stayed absolute.
Act III: Sessions That End Like Adults
Sessions end.
That’s normal.
What isn’t normal is being logged out twice, silently, or mid-flow.
V1.1 fixes that.
Sessions now expire gracefully, with a clear user notification
Duplicate logout calls are gone
No confusion.
No ghost redirects.
No “wait, what just happened?”
Act IV: The Quiet Bugs That Matter
This release also cleaned up the kinds of issues most changelogs hide at the bottom.
We didn’t.
Reporting & Canvas
Business unit connections now persist correctly when reorganising
MiniMap and zoom controls visually match the canvas
Infinite render loops caused by React effects are gone
Safer DOM handling prevents drag-related crashes
Security & Authentication
AI provider API keys are now properly encrypted at rest
CSRF token handling no longer trips TypeScript
Original owners are now immutable, preventing lockouts
Templates use the correct service role instead of anonymous access
These aren’t “minor fixes.”
They’re trust repairs.
Act V: Infrastructure Grows Up
Under the surface, Excalibur became more resilient.
RunPod now uses user-stored API keys, not environment shortcuts
Neo4j starts more reliably with retry logic
Memory usage is tighter on DigitalOcean
Slack integrations no longer break on mismatched variables
The system behaves better under stress.
Which is exactly when it matters.
Act VI: Less Entangled, More Intentional
A few final moves made Excalibur easier to reason about:
Reporting now separates the welcome experience from the canvas
LLM integrations were fully audited and documented
Dependencies were updated and cleaned up with security fixes
No behavioural change for users.
A lot more clarity for the system.
What v1.1 Really Is
This release isn’t about new screens.
It’s about removing fragility.
Excalibur now:
Thinks across providers
Shares without risk
Ends sessions cleanly
Protects ownership by default
Runs more reliably in the real world
V1 proved the idea.
V1.1 makes it sturdier.
And from here, we build forward not sideways.
Welcome to Excalibur v1.1.
For Technical Crowd:
Multi-Provider LLM Support
DGX Cloud Integration: Added NVIDIA DGX hardware as an AI provider option
RunPod Integration: Added RunPod serverless GPU inference support
Dynamic Provider Routing: LLM requests now route to user-configured providers
Provider Logos: Added NVIDIA and RunPod branding to Settings UI
Access Control & Sharing (RBAC Phase 2 & 3)
Module Sharing: Share reports with team members via access control UI
Guest User View Mode: Read-only experience for shared report viewers
Share Link Management: Improved UI for managing report share links
Owner Protection: Prevent accidental owner downgrade when using share links
Session Management
Graceful Session Expiration: Auto-logout with user notification on session timeout
Prevent Multiple Logouts: Fixed duplicate logout calls on expiration
🐛 Bug Fixes
Reporting Dashboard
Business Unit Connections: Connections now persist when dragging away from organization
Canvas Controls: MiniMap and zoom controls now have white background (matching canvas)
Infinite Render Loop: Fixed useEffect dependency issue causing render loops
Block Draggable: Added null safety guards for DOM node operations
Security & Authentication
API Keys Encryption: Fixed encryption for stored AI provider API keys
CSRF Token Hook: Resolved TypeScript error in use-csrf-token
Owner Lockout Prevention: Added immutable
is_original_ownerflagTemplate Security: Switched from anon key to service_role for templates
UI/UX Improvements
Toast Notifications: Use portal to prevent layout shift
Console Cleanup: Suppress harmless errors in production
Server Actions: Fixed import issues in SecurityArchitectureDiagram
Infrastructure
RunPod API Keys: Use user's stored API key instead of environment variable
Neo4j Retry Logic: Added connection retry for container startup reliability
Memory Optimization: Optimized builds for DigitalOcean server
Slackbot Sync: Fixed Neo4j variable names for Slack integration
📦 Dependencies
Package dependencies updated with npm audit fixes
🔧 Technical Improvements
Comprehensive LLM integration audit documentation
Separate welcome and canvas into distinct routes for reporting module
December 29th, 2025
New

The day cybersecurity stopped pretending
Most changelogs start with features.
This one starts with a question.
What if cybersecurity didn’t begin with tools, dashboards, or templates?
What if it began with ground truth?
That question is why Excalibur exists.
And V1 is our first real answer.
Act I: Before the Attack, There Was a Map
Every breach story sounds the same in hindsight.
“We didn’t know this could happen.”
So we built the part most platforms skip.
Threat Modeling, rebuilt from first principles

In Excalibur V1, offensive security starts where it should: understanding the system.
You can drop in:
Architecture diagrams
Confluence documentation
Zoom transcripts from design reviews and incident calls
Excalibur doesn’t just store them.
It connects them.
Behind the scenes, we construct a living mind map.
A neural network of your product.
Assets, trust boundaries, flows, assumptions all tied together.
From that foundation, Excalibur:
Builds multi-framework threat models automatically
Pinpoints exact areas of compromise, not generic risks
Generates unlimited attack vectors, grounded in your actual system
No copy-paste STRIDE tables.
No abstract diagrams that look good and do nothing.
Just a clear answer to: “If I were the attacker, where would I start?”
Act II: Turning Assumptions Into Reality

Threat models are hypotheses.
Attack vectors are questions.

So we made it easy to answer them.
Every attack vector in Excalibur can be pulled into a fully adaptive tabletop exercise.
Not a four-hour meeting.
Not a PDF no one updates.
A focused, one-hour simulation where you:
Walk through the attack step by step
Document controls and gaps as you go
Capture decisions, ownership, and outcomes
Tabletops stop being theatre.

They become rehearsals.
Act III: The Death of the Word Document
Then there’s reporting.
We looked at how pentest reports are written today.
Microsoft Word.
Rigid templates.
RBAC that breaks.
Platforms full of features nobody touches.
So we removed all of that.
Reporting, reimagined

In Excalibur V1, reporting lives on a canvas.
You create a visual, tree-like structure:
Business units
Organisations
Engagements
Reports
Drag. Drop. Done.

Open a report and you’re inside a clean, Notion-style editor that supports:
Text
Images
Video
Audio
Visual attack flows using Excalidraw
You don’t describe the attack anymore.
You show it.
Sharing is simple:
One link
View or comment only
RBAC that actually works
And reporting isn’t limited to pentests.
Teams already use it for playbooks, internal reviews, and security narratives.
Same canvas. New purpose.
Act IV: Templates That Finally Behave

Pentest teams know this pain.
Every client wants a different template.
Every change breaks the workflow.
So we did something obvious.
Templates live on the canvas.
Edit a template once.
Every new report uses it instantly.
Change your mind?
Edit it again.
Create a new report. Done.
No migrations.
No broken formatting.
No wasted time.
You document.
Excalibur handles the structure.
Act V: Where Your AI Runs Is Your Choice
V1 ships in two forms.
Excalibur for SaaS
Threat Modeling
Tabletop Exercises
Visual Reporting
Integrated support for OpenAI and RunPod
More integrations coming
Excalibur for Enterprise
Everything above. Plus something most platforms won’t offer.
On-prem deployment.
Excalibur can run entirely inside your environment on an AI supercomputer:
All language models
All pentest agents
The full platform
No data leaves.
No training on your data.
No cloud dependency.
This is our vision of privatised cybersecurity
where customers keep both the data and the power.
What We Didn’t Build (On Purpose)
We didn’t copy every cybersecurity vendor feature list.
We didn’t chase checkboxes.
We didn’t optimise for demos.
We designed the experience first.
Then built only what mattered.
Every component in Excalibur exists for a reason.
If it wasn’t essential, it was removed.
That’s the constraint we chose.
And it shows.
Who V1 Is For
CISOs who want clarity instead of noise
Pentesters who care about thinking, not formatting
If you believe security should be grounded in reality, not ritual,
you’re in the right place.
This Is Just the Beginning
V1 isn’t “feature complete.”
It’s direction complete.
From here, we extend outward - more integrations, more agents, deeper automation without losing the ground truth that everything is built on.
Cybersecurity doesn’t need more tools.
It needs better thinking.
Welcome to Excalibur
Other Bug Fix and Optimization
🔧 Memory optimization and security audit for npm dependencies
🔧 Production build configuration with npm security fixes
📦 Updated package dependencies with security vulnerability patches
⚡ Optimized Docker memory allocation for DigitalOcean server builds
🚀 Merged staging branch updates to production
🚀 Production deployment configuration updates
🐳 Updated Docker and CI/CD workflows for production deployment
✅ Reporting module verification and quality checks
🐛 Fixed toast notifications causing layout shift in modals
✨ Added RBAC module sharing with Access Control UI
We push updates multiple times a week so be in the know by subscribing to updates.